
IT infrastructure and it solutions services provider. Our firm is an expert to creates an efficient user interface that make user interaction.

Network security is essential in order to boost your services. We develop, migrate & work on applications to ensure that run capably on cloud.

IT infrastructure and it solutions services provider. Our firm is an expert to creates an efficient user interface that make user interaction.

Provides Robust end-to-end Networking solutions . Our team has extensive knowledge, skills and experience in all aspects of network design.

The term "cloud services" refers to a wide range of services delivered on demand to companies and customers over the internet. These services are designed to provide easy.

We are Industry leading office automation providers. We provide an IT management services is for according to an organization’s needs.

The way a network operates is to connect computers and peripherals using two pieces of equipment – switches and routers. These two let the devices connected to your network talk with each other as well as talk to other networks. Routers and switches are the building blocks for all business communications from data to voice and video to wireless access. They can improve a company’s bottom line by enabling your company to increase productivity, cut business costs, and improve security and customer service.
Local area network is a group of computers connected with each other in a small places such as school, hospital, apartment etc. LAN is secure because there is no outside connection with the local area network thus the data which is shared is safe on the local area network and can’t be accessed outside.
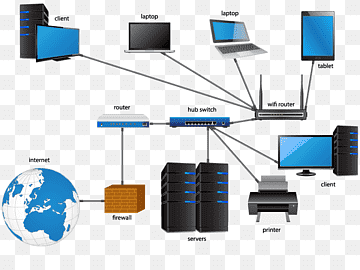
MAN network covers larger area by connections LANs to a larger network of computers. In Metropolitan area network various Local area networks are connected with each other through telephone lines. The size of the Metropolitan area network is larger than LANs and smaller than WANs(wide area networks), a MANs covers the larger area of a city or town.
Wide area network provides long distance transmission of data. The size of the WAN is larger than LAN and MAN. A WAN can cover country, continent or even a whole world. Internet connection is an example of WAN. Other examples of WAN are mobile broadband connections such as 3G, 4G etc.


Wireless Communication Systems also provide different services like video conferencing, cellular telephone, paging, TV, Radio etc. Due to the need for variety of communication services, different types of Wireless Communication Systems are developed. Some of the important Wireless Communication Systems available today are
Spyware is mostly classified into four types: adware, system monitors, tracking cookies, and trojans; examples of other notorious types include digital rights management capabilities that "phone home", keyloggers, rootkits, and web beacons.

Exchanging information on challenges, experiences and goals is a key benefit of networking because it allows you to gain new insights that you may not have otherwise thought of. Similarly, offering helpful ideas to a contact is an excellent way to build your reputation as an innovative thinker.





You get a balance connectivity that stores your data as well as recovers whenever required as well as you and your surroundings remain secure in all the ways.
Redundant components and services in place for any part of a network leads to recover of data in any lost conditions.
When data is backed up, how it is backed up and where copies of the data are stored is a very important decision to be made while designing a network